My Journey From Web2 to My First Code4rena Bounty
Before getting into Web3
My Web2.5 Job
Prior to getting into web3, I had already been working as a developer for ~10+ years. My last job was as a senior developer at a company in the crypto space but it was more like web2.5 than web3. The tech stack was largely web2 but with plans to add some decentralization eventually. Most of the system was written in Go and we were mostly indexing data from Ethereum, other EVM blockchains, and a few other non-EVM blockchains like Solana and Starknet.
During that time, between 2021-2022 , I had been studying Solidity and DeFi on the side since I was interested in developing DeFi protocols. The content I studied included the following in no particular order:
- Cryptozombies.io
- Smart Contract Programmer Youtube channel
- smartcontract.engineer challenges
- Cam Harvey's DeFi Courses
- DeFi protocols' code on Github
- Solidity and Hardhat docs
- Ethereum Engineering Group
- Whiteboard Crypto
- Ethernaut
- Ethereum Whitepaper and Yellowpaper (did not finish the Yellowpaper though)
- Lots of great blog posts on Defi protocols and any blockchain topic I got interested in
My approach to studying then was to learn what I needed so I could read parts of a DeFi protocol's codebase and understand what is being implemented and its purpose (what value it provides to its users).
Taking a Break
In August 2022, I decided to take a break from work and resigned. There were a few factors that led me to this decision, which were mainly:
- stress from a long-running ongoing custody case
- burnt out and feeling an overall sense of being undervalued at work
- I wanted to get deeper into web3
Until November 2022, all I did was just take time for myself, relax, reflect, and do whatever I wanted without worrying about being productive or making a living. My wife was very supportive throughout all this and just let me recover the way I needed to so I could cope with the custody case and figure out my path forward in my career.
Could Not Get a Web3 Job
It was clear to me I wanted to get deeper into Web3 and DeFi and actually write Solidity code and contribute to developing DeFi protocols. By October 2022, I had already sent a lot of applications for smart contract developer and even security researcher roles to a lot of Web3 companies and had done this since even before I resigned from my previous work. None of them panned out and I did not even get to the first screenings. :(
I thought my 10+ years experience as a software developer would help here. It seems others with less work experience were working at some of these companies. For whatever reason, I figured I had to work much harder to prove myself just so I could even get a foot in the door even though I already had all these years of experience. It was a sad realization, but it strengthened my resolve and galvanized my next steps into Web3.
Getting Into Web3
My First Web3 Hackathon
I decided I would build my Web3 portfolio while making some income through web3 project grants and hackathons. I stumbled upon the Reserve Protocol hackathon late October and immediately signed up as a solo developer. From October 25 to December 6, I treated it like my full-time job and built as many collateral plugins as I could. These collateral plugins were smart contracts that extended the protocol to support new collateral such as the CompoundV3 token.
By the end of the hackathon, I had built and submitted collateral plugins for 3 protocols which were:
The results were announced sometime in January 2023 where I got the top 1 in terms of bounties:
Stoked to have won some bounties writing smart contracts in the recent @reserveprotocol hackathon! Transitioning to web3 is slowly paying off 🙏🎉🥂 https://t.co/Z13yPQlDbW
— gjaldon 🏴☠️ (@gjaldon) January 17, 2023
I was finally experiencing a win in my Web3 journey! This was the validation I needed that all my studying was paying off. :)
My First Web3 Project Grant
While doing the Reserve hackathon, I realized that CompoundV3 needed a token wrapper for their rebasing token. This is because protocols are designed to work with standard ERC-20 tokens where balances are static. As a rebasing token, cUSDCv3 (Compound III's token) always maintained a 1:1 exchange rate with USDC but it handled interest accruals for supplying USDC to the protocol by increasing the user's balance of cUSDCv3.
Other protocols that want to use CompoundV3 will need a token wrapper to account for the yield from supplying USDC to CompoundV3. It's possible with a token wrapper since its balance of wrapped tokens remains static, but its exchange rate for cUSDCv3 will continually increase as the supplied USDC accrues interest in CompoundV3. That way, when you redeem your Wrapped cUSDCv3 for cUSDCv3 tokens, you will get the cUSDCv3 tokens you deposited + cUSDCv3 tokens from interest accrual.
In December 2022, I already read news of Compound relaunching its Grants program in January 2023. I verified in the Compound Discord server if the token wrapper project was worthy of a grant and I got positive responses.
January 16, 2023 the Compound Grants Program relaunched and I submitted my grant proposal on January 17. By end of January, my proposal was approved and I spent the next few weeks building it.
I'm happy to announce that my grant proposal to @compoundfinance was just approved by @compoundgrants!
— gjaldon 🏴☠️ (@gjaldon) January 31, 2023
I'll be writing a smart contract for this that I plan to complete within the next 2 months. LFG!!! 🔥
This project grant was my 2nd big win in my Web3 journey. :) As of this writing, the project is still ongoing but have already completed 2 milestones.
Transitioning to Smart Contract Auditing
After the holiday festivities of December and early January 2023, I realized I had a lot of time on my hands before the Compound Grants Program was relaunched. I had already read cmichelio's How To Become A Smart Contract Auditor sometime last 2022 and I already read pwning.eth's million-dollar bug bounties. I always thought it would be nice to try out web3 security and when I got news that Reserve Protocol was launching an audit contest, I thought it was finally time to get into smart contract auditing.
I spent most of January TRYING to audit Reserve while studying web3 security and doing some Damn Vulnerable Defi challenges. The web3 security content I was mostly studying were:
- Consensys' Ethereum Smart Contract Best Practices
- Code4rena Audit Reports
- Trust's Audit Reports
- Andy Li's Interviews
- YAcademy's Youtube Videos
- Some of Secureum's Youtube Videos
I did not watch all of the videos on all the Youtube channels listed and did not read all of the reports. For the reports, I focused on the newer reports and only read the High and Medium findings on Code4rena. For Andy's videos, I only a watched few of his interviews at this time (I watched the rest later). I had to limit the content I consumed because I did not want to get stuck just studying and wanted to get some bounties ASAP! This strategy paid off for me big-time.
Anyway, by the time the Reserve protocol contest ended, I had 0 findings. I only got to spend 3-4 days on it though because of all the studying I did and the Compound Grants application. Although I had 0 findings, the audit was valuable since it showed me what I needed to learn.
Improving My Audit Process
The main thing I learned was that my audit process was haphazard and I focused too much on certain parts of the Reserve codebase. When reading the code, I tried my best to understand it on my first pass and immediately tried to dive deep into one area. I knew I needed a better audit process so I studied the following content:
I rewatched those interviews with a focus on just watching the parts about their audit process and gathered some insights such as:
- focus on understanding and building a mental model of the codebase first rather than finding issues right away
- do multiple passes when reading the code and the first few passes are more of a quick scan
- write comments and notes as you read the code
- make questions for yourself as you theorize attacks or build an understanding of the codebase
- start with the external functions of the main contracts
Zzykxx's blog post was very helpful to show that it was possible to get good results even when just new to auditing. Also, the biggest insight I got was that he won the Chainlink contest because he was 100% focused on it. I applied all these new insights to my next contest.
My First Code4rena Bounty
The Popcorn Contest was scheduled for February 1-8, 2023. I committed myself to the contest from February 2-8 and completely focused on it. Apart from applying my new audit process, I also actively took breaks after some deep focus to try and leverage my brain's background processing (saw this tip on an Andy Huberman video but couldn't find it at the moment).
I will publish a separate blog post on the details of some of the findings and how I got to them since I am unable to share those yet due to Code4rena's terms.
My new audit process helped a lot and I felt my audit was a lot more guided and purposeful. It didn't take long to find vulnerabilities on my first day of auditing Popcorn. By the 3rd day, I was so stoked to have crafted a valid attack that I think may have been my solo High finding for the contest. I was so focused throughout this contest that I caught myself dreaming about code and waking up in the middle of the night excited to audit again! By the time the contest ended, I had submitted 6 High findings, 2 Medium findings, and a Low/QA report. I had a good feeling about this contest.
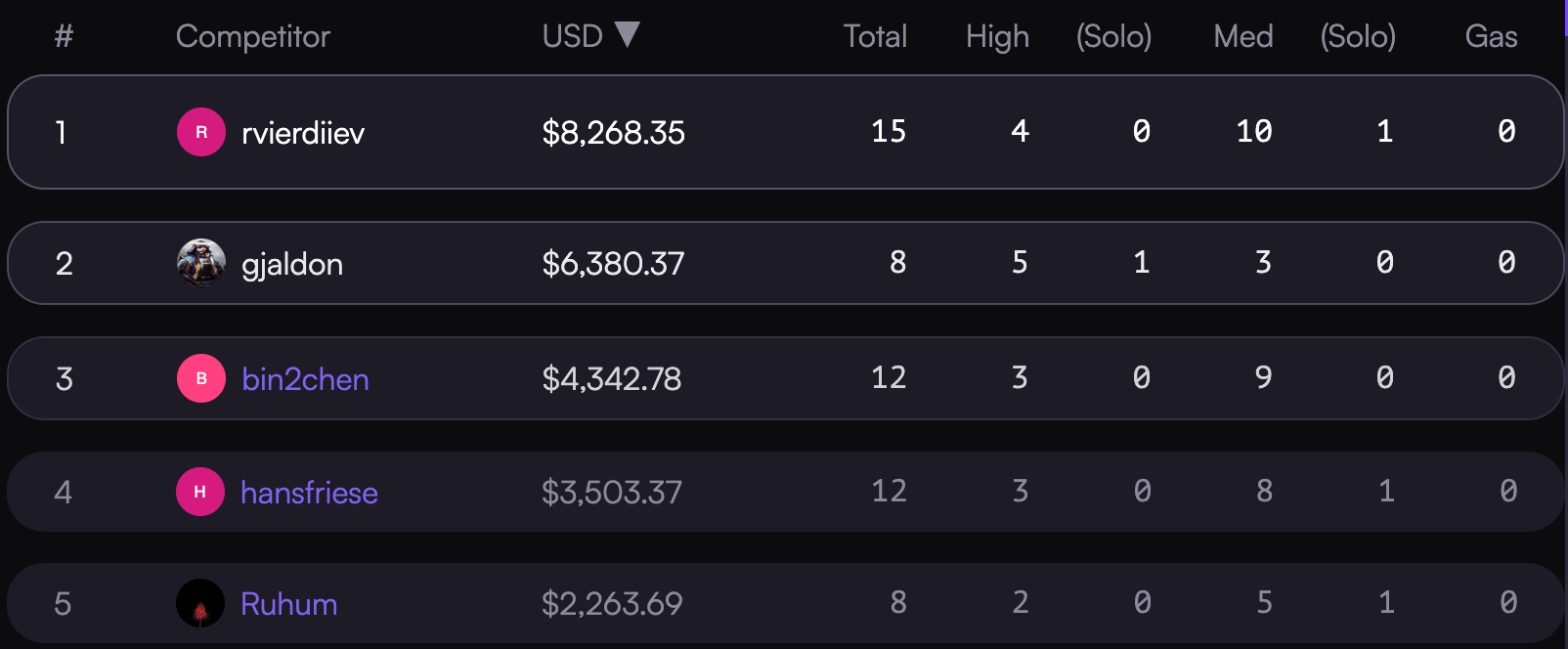
Fast-forward to March 9 when the results were finally released, my results were:
Proud to share my 1st ever @code4rena bounty!
— gjaldon 🏴☠️ (@gjaldon) March 8, 2023
- top 2
- 5 Hs, 3 Ms, 1 solo High
- $6.3K
This is just the start of the journey. I was serious when I said I wanted the top of the leaderboard😎
AMA? 🤣 https://t.co/7TxOeMdSer
Not bad for a first payout. :)
